We’ve said it before, and we’ll say it again: Downloading unverified apps is risky, so unless you are in the business of reviewing them, we suggest you wait for the official apps to go live in your country.
Take the case of Pokemon Go. Less than 72 hours after it was rolled out to Google Play and the App Store in Australia and New Zealand, a malicious APK of the highly anticipated augmented-reality game was released into the wild, security firm Proofpoint reveals.
What it does is install a remote access tool called DroidJack, otherwise known as SandroRAT, on your phone or tablet, so an attacker can take full control of your device. It may even compromise the networks your infected mobile has accessed. You don’t want that to happen, do you?
However, if you were one of those who side-loaded the APK because you couldn’t wait to play Pokemon Go, take a deep breath. Here are ways to find out if your device is compromised.
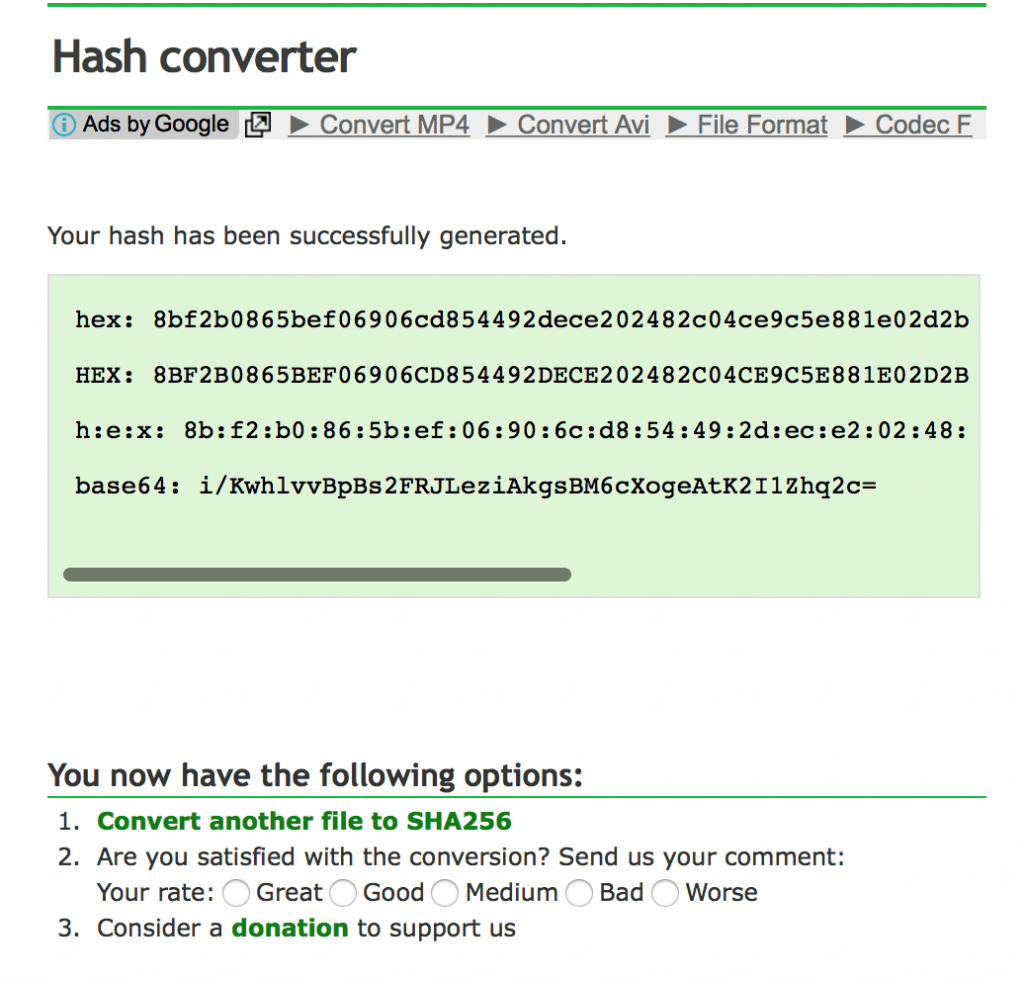
1) Check the SHA256 hash of the APK you downloaded. It’s a string of characters that you can see to verify if an app has been modified. According to Proofpoint, “The malicious APK we analyzed has a SHA256 hash of 15db22fd7d961f4d4bd96052024d353b3ff4bd135835d2644d94d74c925af3c4.”
We examined ours. How? The APK we installed was from APK Mirror. We went to Online-Convert, entered the URL of the file, and converted it. Luckily, the Sha256 hash turned out to be 8bf2b0865bef06906cd854492dece202482c04ce9c5e881e02d2b6235661ab67, which is considered safe by Proofpoint.
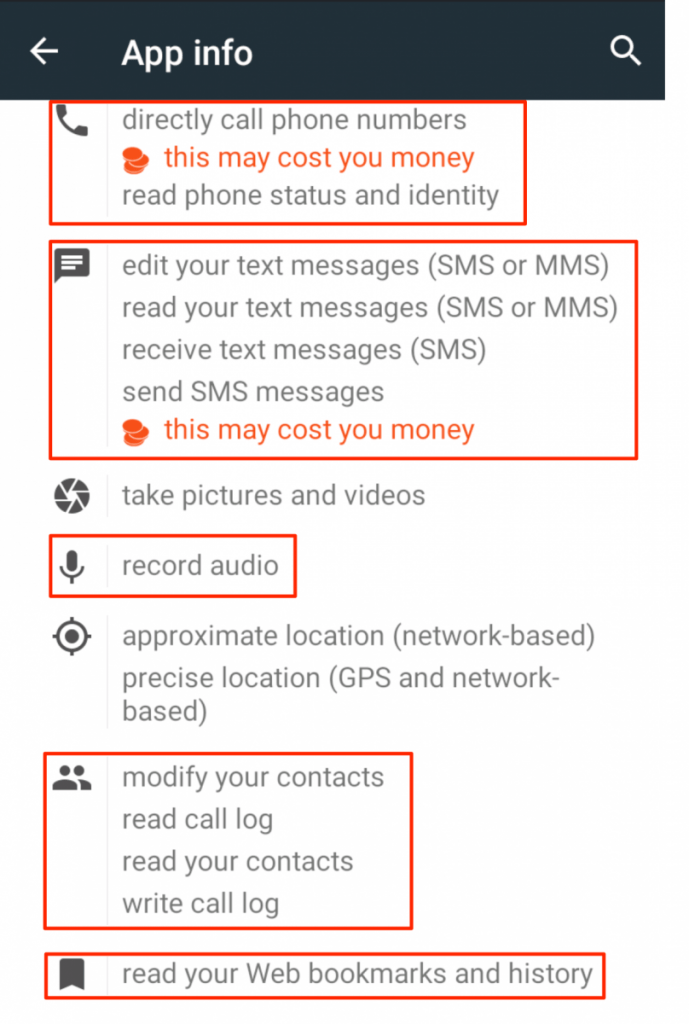
2) Check the Pokemon Go app’s permissions. Go to Settings > Apps > Pokemon Go > Permissions. Here are screenshots of our granted permissions, which are consistent with those Proofpoint finds legitimate:
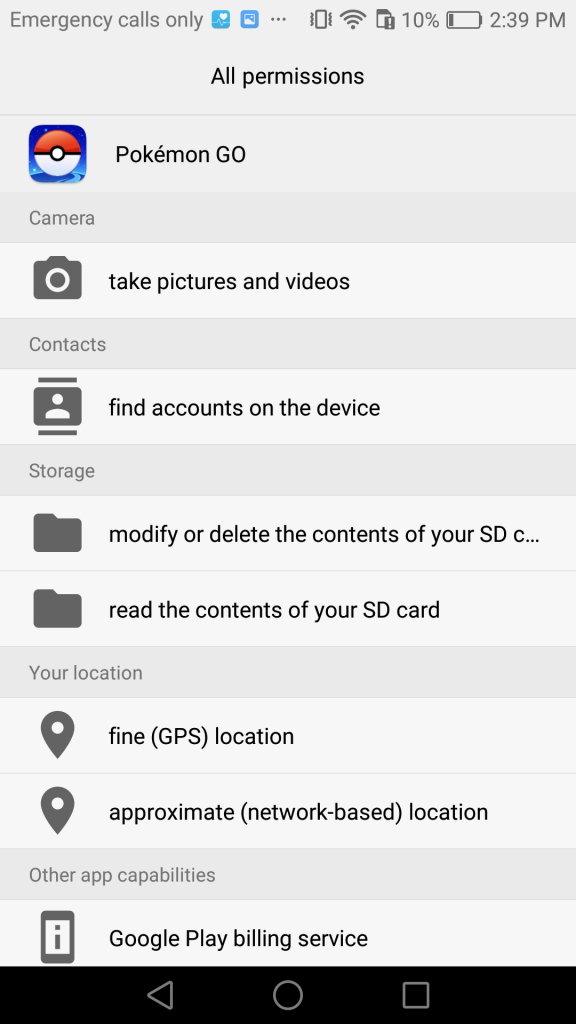
Here’s the first screenshot of granted permissions of the Pokemon Go APK we downloaded from APK Mirror.
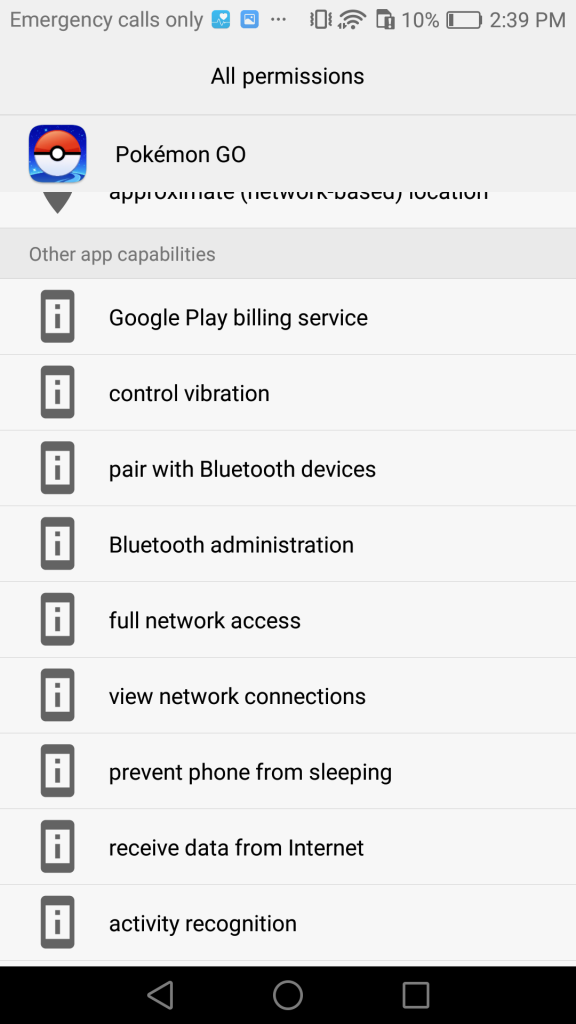
Here’s the last screenshot of granted permissions of the Pokemon Go APK we downloaded from APK Mirror.
Compare those with a backdoored Pokemon Go APK.
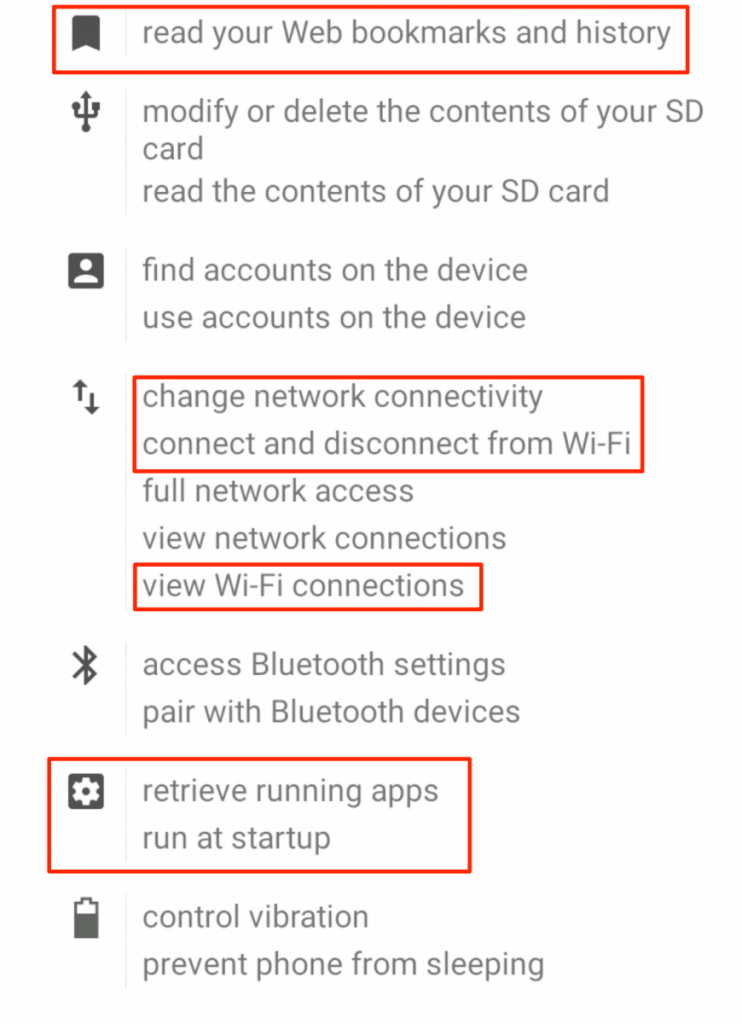
Granted permissions of an infected Pokemon Go APK. This is the second screenshot provided by security firm Proofpoint.
Now, go ahead and check yours!
My take: There’s a reason I don’t include links to unofficial apps in my articles. If you’re not covering the tech industry, remember this rule: Patience is a virtue. Proofpoint said it best: “Just because you can get the latest software on your device does not mean that you should. Instead, downloading available applications from legitimate app stores is the best way to avoid compromising your device and the networks it accesses.”
Story via Motherboard
Images via Proofpoint
Got your own how-tos? Tell us in the comments, or contact us on Twitter.
Share this Post
Related video